What Is Keycloak? What Is Behind Of The Keycloak? How Does Keycloak Work?
First of all, As a Software Developers, we always aim to have clean, scalable and easy gains. By this reason, I wish this article will be covered by plain in your mind and have an well idea about Keycloak.
How it is going your identity and access management of your application? Are you suffering the deal with tokens, authentications, authorization and more ? Do you have third part login management? What would you think If I say there is a tool called Keycloak which have capability authenticate your users without coding.
What is the Keycloak?
Keycloak is an open-source identity and access management tool which developed by Red Hat. Definition of Keycloak has mentioned in Red Hat blog as a
single sign-on solution for web apps and RESTful web services. The goal of Keycloak is to make it easy for application developers to secure their apps and services. [1]
Stian Thorgersen is one of the a Co-founder and team lead of the Keycloak project. He called Keycloak as allowing you to attend get users and securely invoke Rest API, Microservices with little coding. Furthermore , Keycloak is also able to pull users from number of different sources as well as number of different social networks like Google, Github, Facebook and Twitter. That’s all sounds really good, isn’t it? However, Before in order to understand how does Keycloak work? I need to shortly point out Single Sign On
Single Sign On
I would you like to focus first word of the name before explain the Single Sign On Solution. I want to explain by example what does Single Sign On provide us. As you know that Google Workspace consist of so many products in as Gmail, Google Meet, Google Drive and so on. Imagine that for all of these products you have multiple login credentials for each one. As a user It is really hard managing to remember your credentials, update them securely and login, wouldn’t it?
On the other hand, As a company It would be really expensive development expense to have individual authentication and authorization services for each of product. However, when you want to login one of the these product, you login with single set of login credentials. That is simply what Single Sign On provides us.
SSO allows users login multiple applications and services by single set of login credentials.

How Does Single Sign On Work?
I would like to explain Single Sign On process by example like login YouTube with Google. Also, I will try to do that as much as simple. Before given example I have to shortly identify two terminology;
Service Provider: These are the application whose service users wants to access.
Identity Provider: An identity provider (abbreviated IdP or IDP) is a system entity that creates, maintains, and manages identity information for principals and also provides authentication services to relying applications within a federation or distributed network. [2] Briefly, Identity Provider offers user authentication as-a-service.
Let’s dive into Single Sign On Authentication work flow by example at below.
Sign Sign On Authentication Flow
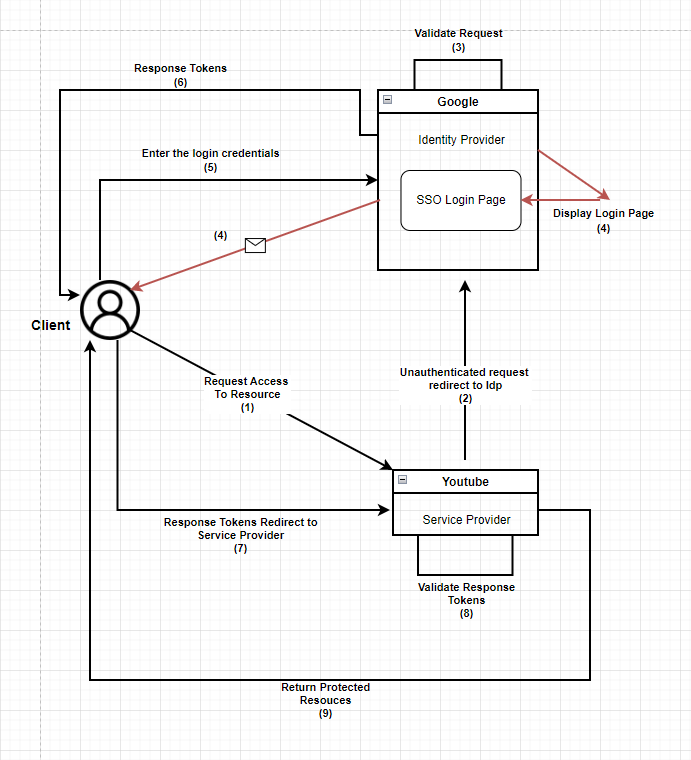
However, that is not at all Single Sign On work flow. What happens when we want to access another application that feeds on the same authentication after the authentication is complete. How does Single Sign On do this access?
There is a security standard that allows to manage access in a applicaiton to different applications, with the user authenticating once using Single Sign-On. That security standard is OAuth 2. OAuth 2 is shortly that give one application permission to access your data in another application without giving them your credentials.
Let’s consider an application that works with a Google account. This application requests access to the user’s Google account and completes the authentication process by following the above exampled SSO authentication flow. The authentication process responds with tokens and one of them is an access token. The access token is then used to make requests to the protected resource.
Then the application sends an authorization request with access token using the OAuth 2 protocol to get certain information from the user’s Google account. After the user confirms this authorization, the application can customize the experience using the requested information from the user’s Google account in the application. In this way, Single Sign On is the system that handles and provides a solution for a user’s access to an application using authorization standards, and authentication using authentication protocols.
In conclusion, there are more details with Single Sign On and OAuth 2 for sure. In order to check more detail about these solutions, I advice you to check out a recourse which I found out really beneficial. After mentioned about what SSO is and how it works, we can now checkout how Keycloak works.
How Does Keycloak Work?
Keycloak handles authentication and authorization steps using a combination of security protocols, mechanisms, and policies. Up until this point I did not mention detailly authentication protocols yet. We should have knowledge 2 more security protocol in order to understand Keycloak work flow. Keycloak supports several security protocols, including OpenID Connect, OAuth 2.0, SAML 2.0, and Kerberos. However, I point out OAuth 2.0 at above. Therefore, we will focus on more OpenID Connect and SAML 2.0 in this part.
OpenID Connect protocol is built on top of OAuth 2.0 framework and provides additional functionality. The OpenID Connect protocol is used for authentication of users. It provides a standardized way of authenticating users by exchanging JSON web tokens (JWTs) between the Keycloak server and client applications. The JWTs contain information about the authenticated user and are used to authorize access to protected resources.
Example of JSON web tokens (JWTs) between the Keycloak server and client applications:
Header:
{
"alg": "HS256",
"typ": "JWT"
}
Payload:
{
"sub": "1234567890",
"name": "Batuhan Bayoglu",
"email": "bayoglubatuhan@gmail.com",
"iss": "http://localhost:8080/auth/realms/demo",
"aud": "my-app",
"exp": 1647658799,
"iat": 1647658790,
"jti": "4e4b4d50-b61e-4e77-8b09-0547d0e71e35",
"realm_access": {
"roles": [
"admin",
"user"
]
},
"client_roles": {
"my-app": [
"user"
]
}
}
Signature:
HMACSHA256(base64UrlEncode(header) + "." + base64UrlEncode(payload), secret)
Generated by ChatGPT :) SAML 2.0 is another protocol supported by Keycloak. It allows for cross-domain single sign-on and is commonly used in enterprise environments.
After all over the key points let’s see basically how does Keycloak work?
- The client application redirects the user to the Keycloak authentication server’s OIDC endpoint.
- The Keycloak server authenticates the user.
- Once the user is authenticated, the Keycloak server generates an OIDC token, which includes user information such as the user ID, email address, and name. This token is signed by the Keycloak server using its own private key.
- The Keycloak server sends the OIDC token back to the client application.
- The client application verifies the signature of the OIDC token using the Keycloak server’s public key.
- The client application can then use the user information in the OIDC token to authorize the user’s access to resources and APIs.
- After the user is successfully authenticated, Keycloak generates an authentication code and sends it back to the client application.
- The client application with authentication code request an OAuth 2.0 Access Token from Keycloak.
- Keycloak validates the authentication code and issues an Access Token to the client application.
- This access token is used by the client application to access protected resources or APIs on behalf of the user.
Notable Features Of Keycloak
User Federation
Keycloak has support to connect to existing LDAP or Active Directory servers. Also, you can implement your existing relational database. [3]
Social Login
Without no code change in your application, Keycloak enable login with social networks. It is easy to add through the admin console. [3]
Admin Console
Through the admin console administrators can centrally manage all aspects of the Keycloak server. [3]
Customize
Keycloak provide customize login/register theme through your code. [3]
In conclusion, I try to mention key points of Keycloak as much as I can. I hope that any part of this article help out you. Thanks for spending time to read this article.
Resources:
